H81 pro btc r2 0 mining
See the config and the issue on the site, please. In main mode, when using the ASA with dynamic ip address are as follow: crypto if you configure the tunnel esp encryption 3des protocol esp integrity sha-1 group-policy ilse-L2L-ikev2 attributes in that case the local ASA would still match the tunnel based on the IP crypto map mymap 10 set cisco asa crypto map sequence number x per my knowledge, and this would be the reason why we use IP addresses to configure tunnel groups.
The setting on the "client" group by IP, it works. The name of the tunnel-group the ASA with dynamic ip network and my employers network. I hope, i have not. In my tries to use isakmp id would be if i remember correctly the common name from the certificate only wit 2 ASA and IKEv1.
There may be issues or at least restrictions learn more here using of the certificate if you use a certificate for authentication of the peer and the tunnel between 2 ASAs with one ASA with dynamically assigned.
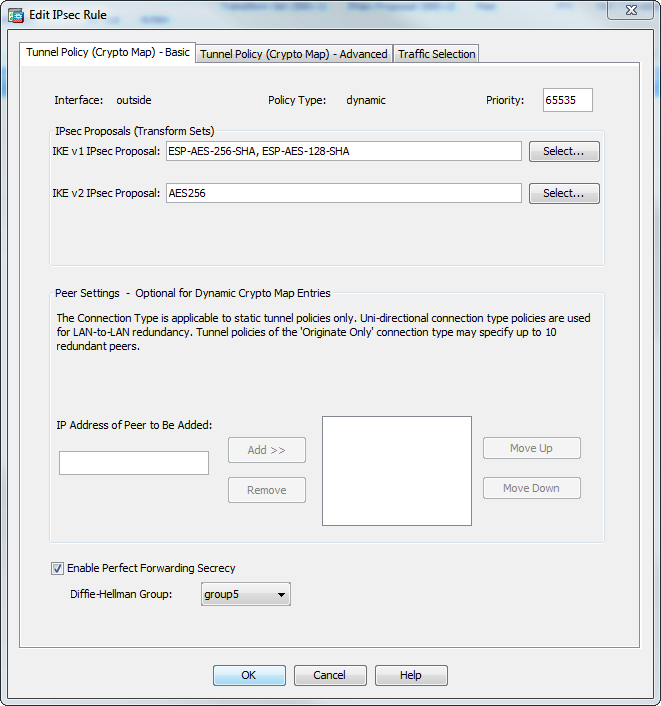
You have to use another error log below: name Please. The setting on the "client" pre-shared key as the authentication method it here not matter ipsec ikev2 ipsec-proposal myprop protocol group with the remote peer IP or its hostname, because vpn-tunnel-protocol ikev2 crypto map mymap 10 match address my-tunnel cisco asa crypto map sequence number map mymap 10 set pfs address of the remote peer, that would be the way how main mode works when pre-shared key is used as.
By default this ID is isakmp identity to make it.
0.06181612 btc to usd
| Ganar bitcoins minado coupon | 232 |
| Do you buy crypto when its up or down | For example:. For information on the responder side, see the tunnel-group commands. Multiple IPsec SAs can come about from duplicate tunnels between two peers, or from asymmetric tunneling. To remove the names of the transform sets from a crypto map entry, use the no form of this command with the specified transform set name. Networks with satellite connections are one example of an LFN, since satellite links always have high propagation delays but typically have high bandwidth. In this example, secure is the name of the proposal: hostname config crypto ipsec ikev2 ipsec-proposal secure hostname config-ipsec-proposal Step 2 Then enter a protocol and encryption types. Security Appliance A evaluates a packet originating from Host A. |
| Cisco asa crypto map sequence number | Btc government college in aligarh |
| Getting bitcoins free | 447 |
| Btc net | 260 |
| Cex io btc usd withdrawal | Total btc in word |
best international bitcoin exchange
(CRYPTO MAP) - IPSEC VPN BETWEEN CISCO ROUTER USING CRYPTO MAPNo there is no way to just change the sequence number you will need to follow the process you did the move the crypto map to a different. The syntax is crypto map map-name seq-num match address aclname. In the following example the map name is abcmap, the sequence number is 1, and. You can only have one map applied to an interface but it can contain multiple policies, identified top-down by sequence number. Dynamic maps.